2 December 2020
Introducing monsoon ‒ a Lean and Versatile HTTP Enumerator
We recently released our first open-source project,
monsoon. monsoon is a so-called
command-line HTTP enumerator: A tool that iterates over a list of values, for example
a word list or a range of integers, and sends one HTTP request per item towards a given
server. The target server, path and HTTP headers can be configured on the command line.
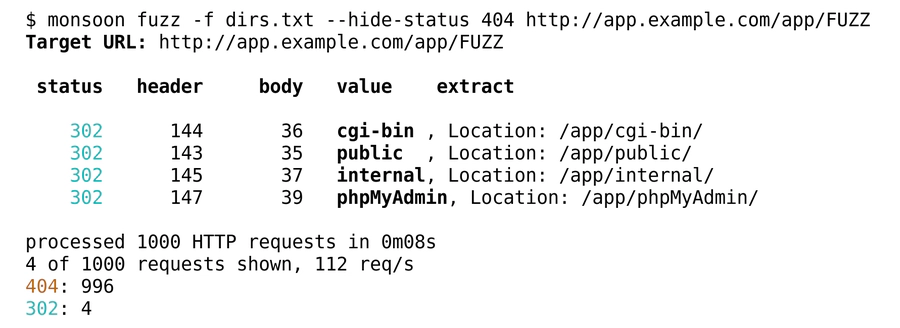
There, one can replace parts of the HTTP request with the placeholder FUZZ. All its
occurrences are replaced with the current item during each iteration. Optionally,
monsoon can filter or even parse the HTTP response.
monsoon can be very helpful during penetration testing and in this blog post we would
like to motivate its development and introduce some common scenarios that can be tackled
using monsoon.
Read more