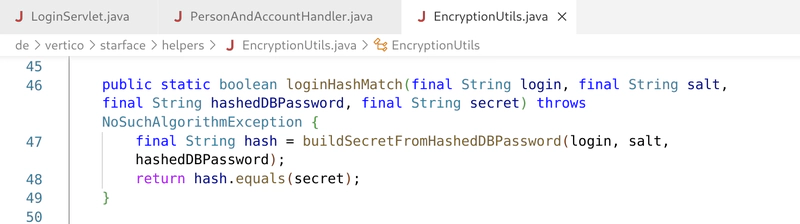
Bringing Monsoon to the Next Level
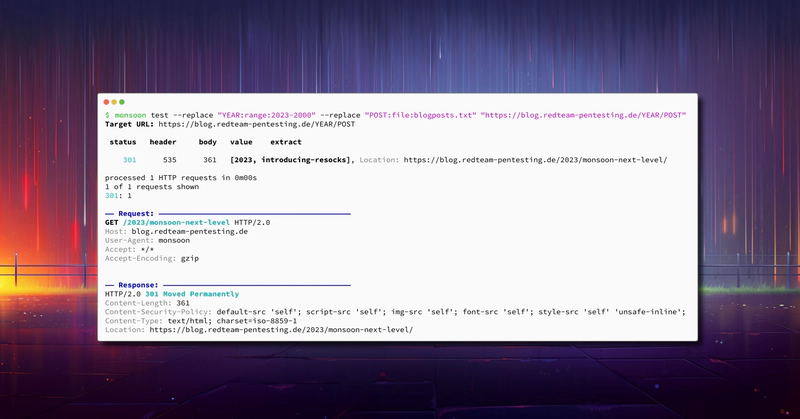
We’ve just a released a major update for our HTTP fuzzer monsoon with many new features and improvements. In this blog post we will cover these changes in detail. If you haven’t heard about monsoon, you should start with our announcement blog post where we explain the purpose of monsoon and show how it can be used in various scenarios. With that said, let’s jump into the changes.
Read more