12 July 2023
Bringing Monsoon to the Next Level
We’ve just a released a major update for our HTTP fuzzer monsoon with many new features and improvements. In this blog post we will cover these changes in detail. If you haven’t heard about monsoon, you should start with our announcement blog post where we explain the purpose of monsoon and show how it can be used in various scenarios. With that said, let’s jump into the changes.
Replace Parameters - Fuzzing Just Got Exponentially More Powerful
The core of the monsoon fuzz
command is the fuzz parameter (duh!), which previously replaced the string
FUZZ with either a range of numbers (--range) or a wordlist (--file).
However, one of the pain points of both us and the
community was that it
was not possible to specify multiple fuzz parameters at once. Our newest version
of monsoon solves this issue
with the brand new command line option --replace that you can pass multiple
times allowing you to fuzz in multiple dimensions. The string that should be
replaced in each request must also be specified, so
monsoon can distinguish the
different strings in the requests.
One of the typical use cases of multiple simultaneous fuzz parameters is brute-forcing of credentials. Here it is in action:
As you can see, the admin’s credentials don’t stand a chance against the new
--replace feature. To use it, you first have to specify the fuzz key
word which will be replaced (in the latter case PASS), the parameter type
(file) and in this case the filename. But with great power comes
great responsibility, so keep in mind that the number of combinations will grow
exponentially with multiple --replace options. This means you need to check
the size of your fuzz ranges and the number of entries in your world lists
carefully if you want to find the right login before the heat death of the
universe. If this scares you, you can still use the old options (like
--range or --file), but you cannot mix the old options with --replace.
Formatted ranges (--range with --range-format) can also be used like this:
--replace PIN:range:0-9999:%05d.
Static Value Replacer - Why Do You Even Need This One?
We also added the new fuzz parameter type value that replaces the fuzz keyword
with a static value. You are probably asking yourself: “Why would I need to
replace something with a static value if I could just change it directly right
away?”. Well, this actually makes more sense when you are using a template file
for your request and run monsoon
multiple times and your login token keeps expiring. With a static replace value
you can edit your template file once like this:
GET /api/FUZZ HTTP/1.1
Host: example.com
Cookie: token=TOKEN
Now you don’t need to update your template every time as the token is passed via the command line:
$ monsoon fuzz 'https://example.com' --template-file template.request \
--replace FUZZ:file:api.txt --replace TOKEN:value:d3b07384d113edec49eaa6238ad5ff00
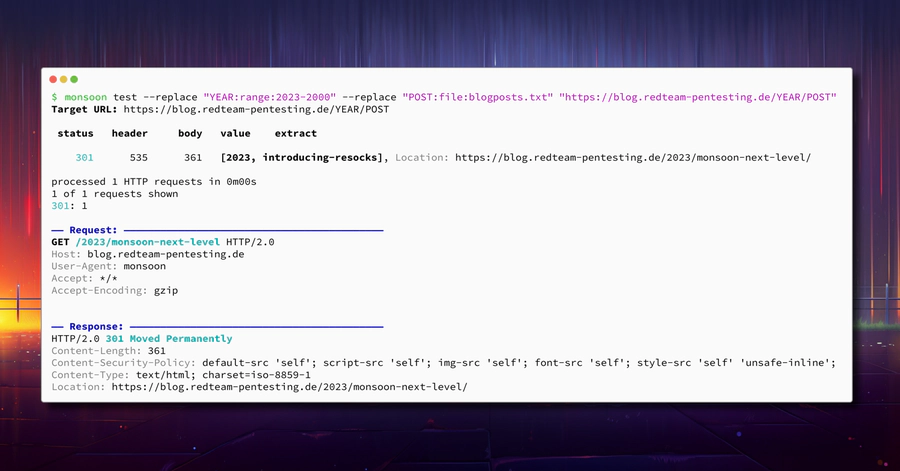
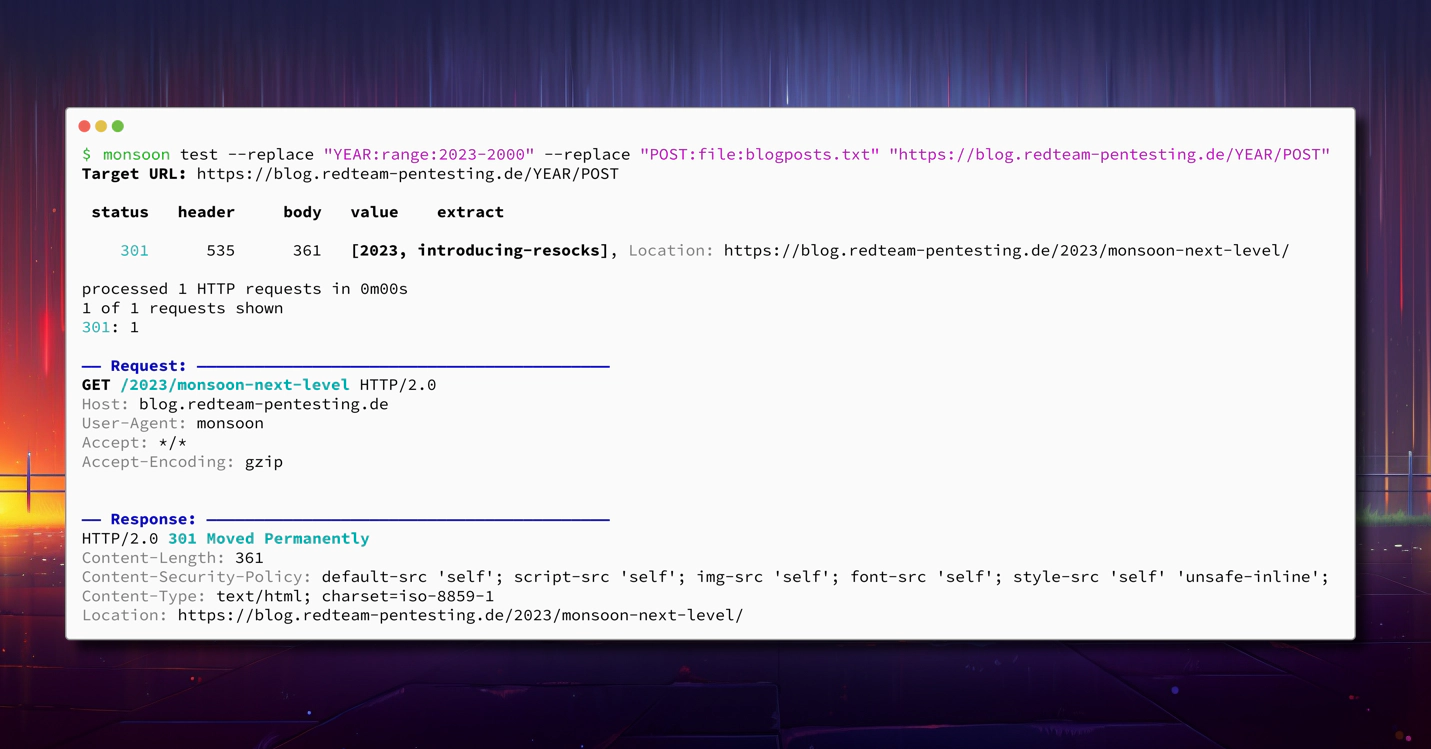
Look Under the Hood With the Overhauled “test” Command
If you have used monsoon’s
test command before, you have probably noticed that it previously has not
gotten as much love as the fuzz command. That’s why we have rewritten the
entire command from scratch. The test command was intended to help you debug
your fuzz commands by sending a single request and dumping the request and the
response. Previously, however, when switching between fuzz and test it was
required to remove all command-line arguments that are irrelevant for a single
test request (like --threads for example). Now it is as simple as swapping the
verb fuzz with test. All options that don’t apply in this mode are simply
ignored and the first value of each fuzz parameter is used to send a single
sample request.
Remember the showcase of the --replace keyword where we discovered the admin
password? Such a complex invocation can now be easily debugged like this:
As you can see, in addition to monsoon’s typical request table, the sample request and its response are also rendered in beautiful colours ✨
Long Request Detection - Targeting the Weak Ones
Due to the highly parallel nature of fuzzing, it was previously almost
impossible to detect really slow requests. However, sometimes abnormally slow
requests are exactly the requests that are interesting. For example, they can
possibly hint at easily exploitable denial-of-service vulnerabilities.
Fortunately, monsoon now has you
covered by marking such requests. By default,
monsoon will mark any request
that took more than five seconds to complete, however this can be configured as
needed with the --long-request option. Enough talk, let’s see it in action:
But Wait, There’s More…
We’re still not done yet. There are still some minor features, improvements and fixes we managed to cramp into the new update:
- 🔄 Reverse Ranges: You can now count backwards in
--rangeparameters by swapping the start and end like this:--range 10-0 - 🔧 Overhauled Extract-Pipe Function: The commands specified in
--extract-pipenow run in parallel which can improve the overall speed during fuzzing significantly. Also errors are now displayed and the current fuzz values are passed to the command as the environment variables$MONSOON_VALUE(only the first value) and$MONSOON_VALUE1-$MONSOON_VALUEN. - 🗝️ Insecure Ciphers: We pentesters really do encounter some ancient
webservers from time to time. You can now use
--insecure-ciphersuitesto enable some additional pre-historic TLS ciphers to be able to talk to geriatric webservers. - 🐌 Timeouts: You can now configure fine-grained timeouts using
--connect-timeout,--tls-handshake-timeoutand--response-header-timeout. - 🌈 Colours on Windows: No, not Window Color! Support for coloured output for our Windows users!
- 🗜 Decompression: Sometimes you just have to decompress. That’s why we fixed an issue where responses were previously not automatically decompressed in template mode.
- 📈 More Robust Template Parser: The template parser (used when
--template-fileis specified) now parses HTTP/2 version strings correctly. Currently, however, the HTTP version string in the template does not actually affect the protocol that is used. - ℹ Version Command: Find out which version of
monsoon you are using with the
new
monsoon versioncommand. - 📦 Pre-Built Binaries: Last but not least, you can now find pre-built binaries for various operating systems at the releases page.
Open Source at RedTeam Pentesting
That’s about all we can say about the new monsoon. If this is not enough for you, take a look at our name resolution spoofer pretender (blog post) or our mTLS-encrypted back-connect SOCKS proxy resocks (blog post). We are always proud to be able to contribute to the InfoSec community by releasing our offensive tools, so stay tuned for future releases which we announce here and on our social media.
